-
Automate compliance, simplify security.Pricing:
- Free Trial
#Monitoring Tools #Governance, Risk And Compliance #Compliance
-
Unicis Open-source Trust Management platform offers automated solutions that streamlines the process of identifying vulnerabilities, conducting audits, and achieving regulatory compliance.Low-cost GRC platform for effortless Security and CompliancePricing:
- Open Source
- Freemium
- Free Trial
#Cyber Security #Governance, Risk And Compliance #Risk And Compliance
-
Cybereason is an automated endpoint detection and response platform that identifies all the elements of cyber attacks.
#Cyber Security #Security & Privacy #Email Cybersecurity Solution
-
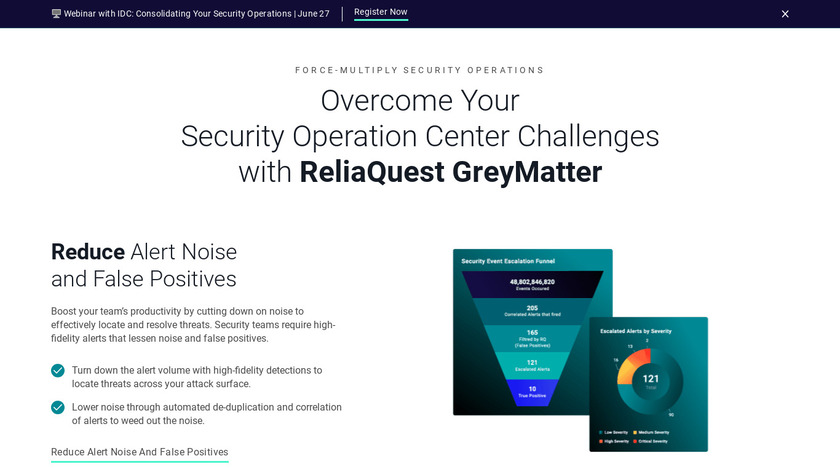
Increase visibility, reduce complexity, and manage risk across your existing tools with comprehensive protection unified under a single security operations platform.
#Cyber Security #Security Operations #Threat Detection And Prevention
-
Know you are protected: Safely test against real threats
#Cyber Security #Email Cybersecurity Solution #Risk Management
-
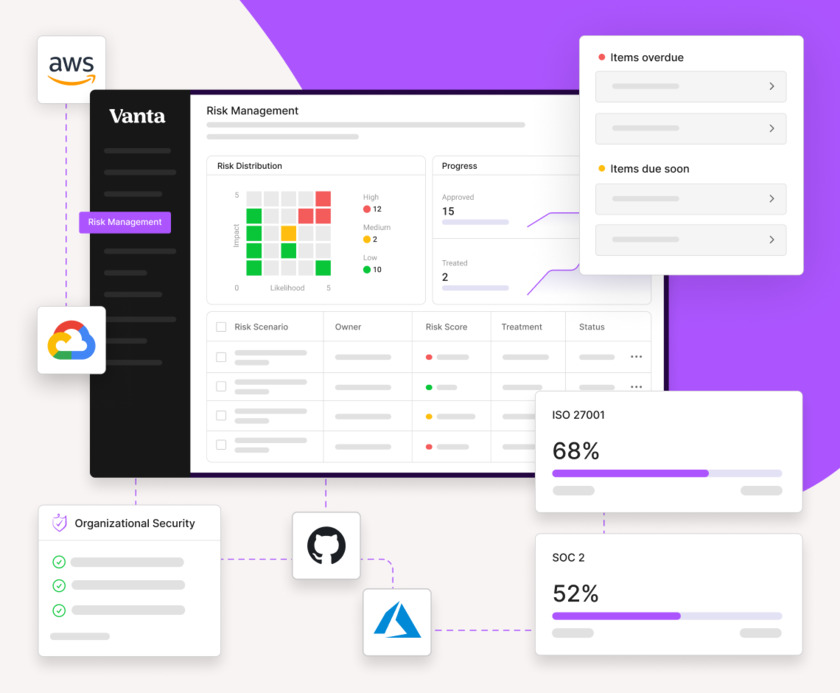
Get enterprise ready with SOC 2 and ISO 27001 compliance
#SaaS #Privacy #Developer Tools 2 social mentions
-
RiskIQ enables organizations to maintain the integrity of web and mobile properties by detecting instances of malware, impersonation and defacement used to commit fraud and violate users’ privacy.
#Risk Management #Security & Privacy #Cyber Security
-
ThreatConnect’s intelligence-driven security operations is the only solution with intelligence, automation, analytics, and workflows in one platform.
#Monitoring Tools #Cyber Security #Security 1 social mentions









Product categories
Summary
The top products on this list are Vanta, Drata, and Unicis.
All products here are categorized as:
Software and tools focused on protecting computer systems, networks, and data from digital attacks, unauthorized access, and other online threats.
Systems for identifying and managing potential project risks.
One of the criteria for ordering this list is the number of mentions that products have on reliable external sources.
You can suggest additional sources through the form here.
Related categories
Recently added products
FiniteState.io
RiskAssessmentAI
NextDimension
BreachAware
Securiwiser
Asimily
CORIZANCE
Censinet
SecurityStudio
SmartTrust.io
If you want to make changes on any of the products, you can go to its page and click on the "Suggest Changes" link.
Alternatively, if you are working on one of these products, it's best to verify it and make the changes directly through
the management page. Thanks!